South Africa
ETHIOPIA
Mail for information:
We place a high priority on protecting your privacy. For this reason, MapleLMS commenced the difficult process of obtaining SOC 2 compliance and passing the SOC Type 2 Security, Availability, and Confidentiality examination. It’s a standard that not many in the LMS sector can receive.
Certification for SOC 2 is granted by external auditors. Based on the established systems and procedures, they evaluate a vendor’s compliance with one or more of the five trust principles.
Definition of SOC 2
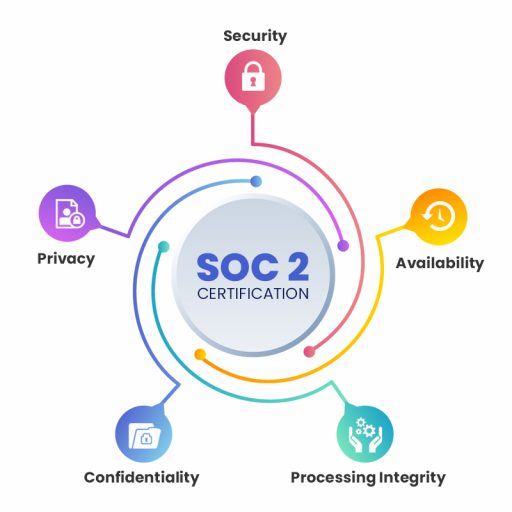
SOC 2 developed by the American Institute of CPAs (AICPA), establishes standards for handling customer data according to five “trust service principles” including:

Security
Protecting system resources from unwanted access is referred to as the security principle. Access controls aid in preventing possible data theft or removal, improper alteration or disclosure, software misuse, and system abuse.Availability
The accessibility of the system, goods, or services as required by a contract or service level agreement (SLA) is referred to as the availability principle. As a result, both parties determine the lowest performance level that is acceptable for system availability.Processing Integrity
The accessibility of the system, goods, or services as required by a contract or service level agreement (SLA) is referred to as the availability principle. As a result, both parties determine the lowest performance level that is acceptable for system availability.Confidentiality
If only a certain group of people or organizations are allowed access to and disclosure of the data, then it is considered confidential. Data meant exclusively for company employees, business plans, intellectual property, internal price lists, and other sensitive financial information are a few examples.Privacy
The privacy principle covers how personal information is collected, used, retained, disclosed, and disposed of by the system in accordance with privacy notices from organizations and the standards outlined in the generally accepted privacy principles (GAPP) of the AICPA.
SOC reports come in two types:
- Type I explains a vendor’s systems and if the relevant trust principles can be met by the way they are designed.
- Type II describes those systems’ operational efficacy in detail.
Why SOC 2 Compliance is Important for LMS?
MapleLMS has a stronger data security equilibrium than its competitors without a SOC 2 report because it complies with all 157 controls in the SOC 2 Type 2 standard. MapleLMS clients can feel confident that we take great care to protect their data because we passed the SOC 2 Type 2 examination.
We at MapleLMS ensure that safeguards for protecting personal information are not only in place but also effective by fulfilling SOC 2 Type 2 examination standards.
FAQs
The security, availability, processing integrity, confidentiality, and privacy of a service provider’s systems and controls are evaluated by an independent audit report called SOC 2 (Service Organization Control 2). It shows how well a service provider handles client data.
The software company providing the software as a service (SaaS) can go through the audit and become SOC 2 compliant for their particular offering, but the software itself cannot be SOC 2 compliant. This indicates that their customer data management controls have been evaluated and found to be compliant with industry standards.
The requirements for compliance differ based on your industry, legal requirements, and contractual obligations. Although it’s not always necessary, many businesses, particularly those handling sensitive data, prefer or demand that their LMS vendors and other service providers comply with SOC 2 standards.
The specific controls needed are determined by the Trust Service Principles (TSPs) selected for the audit as well as the type of SOC 2 report (Type 1 or Type 2). Security, Availability, Processing Integrity, Confidentiality, and Privacy are the five core TSPs. A variety of controls for data security, change management, incident response, access control, and other areas are covered by each principle.
SOC 2 compliant services are advantageous for any organization that handles or stores sensitive data, especially those in the government, healthcare, education, and financial sectors. This is crucial particularly if you have to comply with data protection laws like GDPR or HIPAA.